IPSec einrichten (Linux)
Please note:
The Mobile Pools IPSec Gateway is an open source solution of the strongSwan project and uses the new IKEv2 standard in IPSec. This page describes two different options for setting up the IPSec protocol. However, only one variant of this is required, either StrongSwan or StrongSwan NetworkManager GUI. |
strongSwan
Installation
Most distributions deliver installation packages for Strongswan. Otherwise it is possible to download them in the internet (e.g. for OpenSUSE). It is also possible to download the source code from strongswan.org and to compile it by yourself.
IPsec Configuration
For configuration some data files must be edited. /etc/ipsec.secrets must contain the following (besides these entry's there should at most be some comments in the data file):
/etc/ipsec.secrets
: RSA key.pem "<CERTIFICATE-PASSWORD>"
Furthermore the file /etc/ipsec.conf must be adjusted. As well as above there shouldn't be any entries except the ones shown below, unless there are further IPSec connections. Please note that you must enter your account name in the prescribed position.
/etc/ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
strictcrlpolicy=no
nat_traversal=yes
charonstart=yes
plutostart=no
# Add connections here.
conn %default
keyexchange=ikev2
left=%defaultroute
leftsourceip=%config
leftcert=cert.pem
leftid=[ACCOUNT]@informatik.uni-freiburg.de
leftfirewall=no
rightsubnet=0.0.0.0/0
rightid=root@vpn-mopo.vpn.uni-freiburg.de
auto=add
conn mopo
right=10.1.0.2 # MoPo via WLAN
conn mopo-home
right=132.230.151.174 # MoPo via Internet
Installing the x.509v3 certificate
The certificate that has been created and downloaded in step 3 must now be formated for its use in Linux, because the current IPSec implementations unfortunately don't support any keys in PKCS12 format. For this purpose the program OpenSSL is necessary, which is available in all current Linux distributions.
The following instructions extract the relevant certificates and the PrivatKey from the PKCS12-certificate. Therefor you must enter the password you have chosen before. For the last command you even have to enter the password three times.
Note: the option "-legacy" is only required with Ubuntu 22.04 or openssl version 3.x
openssl pkcs12 -in cert.p12 -legacy -clcerts -nokeys -out /etc/ipsec.d/certs/cert.pem
openssl pkcs12 -in cert.p12 -legacy -cacerts -nokeys -out /etc/ipsec.d/cacerts/root.pem
openssl pkcs12 -in cert.p12 -legacy -nocerts -nodes | openssl rsa -des3 -out /etc/ipsec.d/private/key.pem
Now everything should work. IPSec can be started with "ipsec start". Subsequently the connection to mopo can be established with "ipsec up mopo" or "ipsec up mopo-home" , depending on where you want to get access from (either from the WLAN of the university or from outside via internet). With "ipsec down" the connection is canceled.
strongSwan NetworkManager GUI
Prerequests
- Install needed packages:
In order to set up the "MoPo VPN Connection" through the "NetworkManager Applet" in Gnome based Desktops, we need to install the strongSwan Network Manager plugin. Most distributions deliver installation packages for the strongSwan plugin.
With Ubuntu or Debian based OS, install the package "strongswan-nm"
Otherwise the plugin can be build from source. Detailed instructions can be found at the strongSwan Website under User Documentaion - NetworkManager.
- Connect to the Internet:
Connect to the wireless network and set the MTU-Size (Max Transfer Unit) to "1000 bytes"
Note: The MTU setting can be found under "Network Connections" (right click nm-icon, click on "Edit Connections .."), Tab "Wireless", then choose the "WLANuni-fr" connection
Configuration of the VPN connection
Click on NetworkManager-Icon in the Pannel Area -> VPN Connections -> "Configure VPN ..."
Registercard "VPN"
-> "Add" -> choose: "IPSec/IKEv2(strongswan)" -> "Create"
Create VPN Connection:
To set up the VPN connection, the "gateway certificate", the "x509 user certifciate" and its corresponding "private key" is needed:
The "gateway certificate" can be found in the "CRLs & CA-root certificates" section or directly >>here<<.
(SHA1 Fingerprint=74:9E:99:CE:92:D8:EA:46:27:C9:20:14:D7:C8:C0:8D:4C:39:C0:3C)
The "x509 user certificate" and its corresponding "private key" can be extract from the PKCS#12 file (cert.p12). The users PKCS#12 file is downloadable in the "certificate management" section. Here are the commands for extracting the needed certificates:
Note (1): you will be asked for the passphrase for the private key
Note (2): the option "-legacy" is only required with Ubuntu 22.04 or openssl version 3.x
openssl pkcs12 -in cert.p12 -legacy -clcerts -nokeys -out cert.pem
openssl pkcs12 -in cert.p12 -legacy -nocerts -nodes | openssl rsa -des3 -out key.pem
Note: save the three file in your home in a new director, e.g. mopo.
The following screenshot show how to set up the MoPo vpn connection: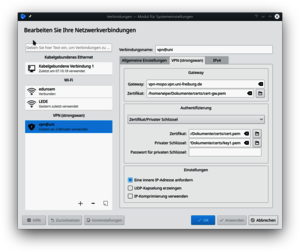
- Starting/stopping VPN Connection
Click on "NetworManager Icon", "VPN-Connection" and "Mobile Pools" will start the connection.
After starting the connection, you will be asked for the passphrase of the private key

